Understanding QUIC: How It Solves TCP’s Limitations and Improves HTTP/3 Performance
Introduction
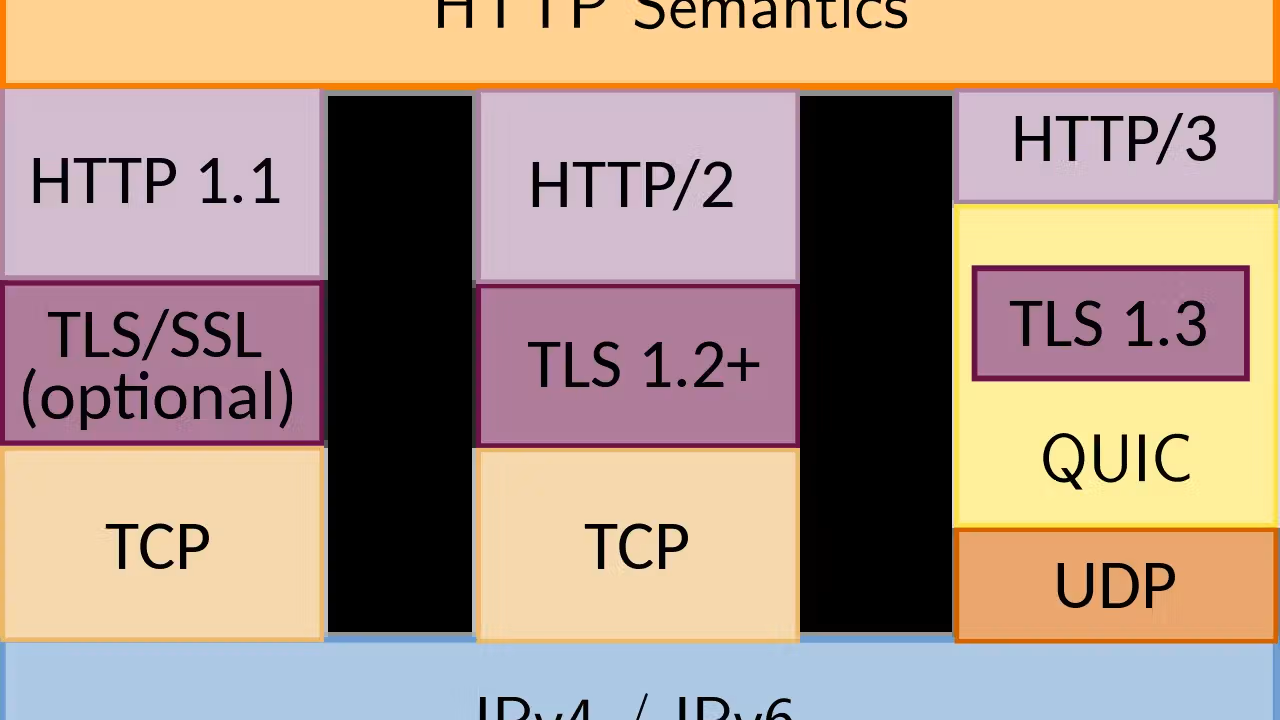
With the rise of HTTP/3, the QUIC protocol has become a critical component of modern web performance. But what makes QUIC different from traditional TCP-based HTTP/2, and how does it overcome head-of-line blocking? Let's break it down in simple terms.
HTTP/3 is Built on QUIC and Requires TLS 1.3
Unlike previous versions of HTTP, HTTP/3 is fundamentally built on top of QUIC, which in turn requires TLS 1.3 for encryption. This means that:
This integration results in faster and more secure connections compared to HTTP/2 over TCP.
QUIC vs. TCP: The Handshake Process
One of QUIC’s most significant advantages is its fast handshake process compared to TCP + TLS. Unlike traditional TCP, which requires multiple round trips for connection establishment and TLS negotiation, QUIC combines these steps into one.
?? Q: Does this mean QUIC completely skips SYN packets and jumps to SSL handshake?
?? Q: What would I see in Wireshark for QUIC?
?? Q: 1-RTT or 0-RTT?
?? Q: What about TLS renegotiation?
Can Servers Request Client Certificates in TLS 1.3?
TLS 1.3 still supports client authentication, but with differences:
?? Q: So, a server using QUIC can’t ask for a client certificate later?
How QUIC Solves TCP’s Head-of-Line Blocking Issue
HTTP/2 over TCP suffers from head-of-line (HoL) blocking because:
QUIC solves this by:
?? Q: Is this because QUIC uses UDP?
?? Q: Does UDP support SACK by default?
Conclusion
QUIC is a game-changer for web performance, offering:
? Faster handshakes (1-RTT or 0-RTT)
? No TCP head-of-line blocking
? Built-in encryption with TLS 1.3
? Improved reliability & congestion control over UDP
As HTTP/3 adoption grows, QUIC will continue shaping the future of internet communication. Have you explored QUIC in your projects? Let’s discuss! ??
#QUIC #HTTP3 #Networking #TLS13 #Performance #Cloud #WebDevelopment
Cisco Technical Consultant Engineer | Wireless Technology | Network and Security Engineer
1 个月Very helpful, allah ya3teek el 3afyeh bro ??