TCP versus UDP
TCP versus UDP
OSI Reference Model is the first lesson of Cisco CCNA 200-301. There are seven different layers in OSI Model. Teh fourth one, Trasport Layer is one of the important layers of OSI Model. In transport layers, there are various protocols. Three important transport layer protocols are given below:
?
Here, we will focus on two of protocols, UDP and TCP. We will compare TCP vs UDP and we will learn the key characteristics of these protocols. Below, you can find a tablo that shows the summary of these characteristics.?
________________________________________
Comparison of TCP and UDP
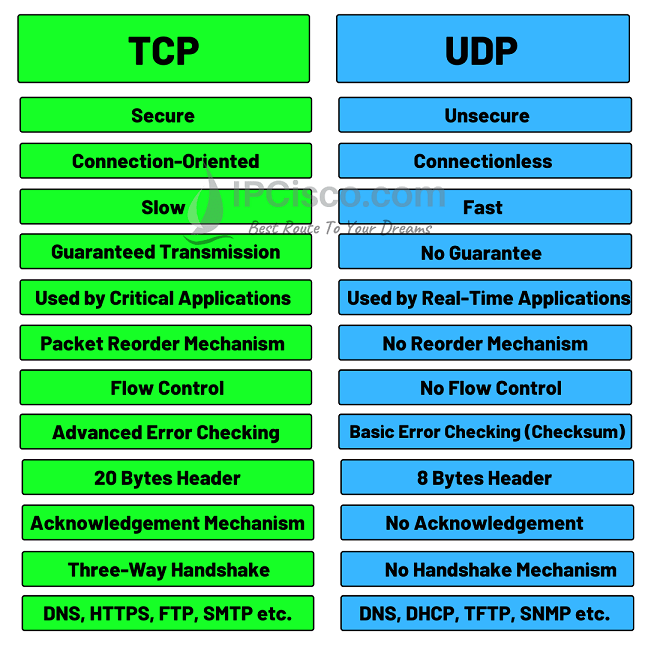
First of all TCP is more secure than UDP. But SCTP is also more secure than TCP. There are different security alternatives for UDP also. But in general, we can say that SCTP is the most secured one, TCP is secure but UDP is not secure transport protocol.?
?
If we compare TCP versus UDP about connection, TCP is a connection-oriented protocol while UDP is connectionless protocol. If an applicaiton is using TCP, a TCP session must be established with three-way handshake. There is no handshake mechanims for UDP.?
?
About speed, when we compare UDP and TCP, UDP is faster protocol than TCP. So, in real time streaming or for voice traffic, UDP is prefered instead of TCP.?
?
When you send a packet with TCP, it is a guaranteed transfer. This means that, you packet will be received from the other end. If it do not receive it, TCP mechanism send this packet again. But there is no such a mechanism in UDP. So, TCP is used for critical applications but UDP is preferred by the applicaitons that tolarate packet loss.?
?
There is no packet reordering mechanims and flow control mechanism in UDP. But TCP provices these key services. And there is no ACK mechanism in UDP. BUt TCP has ACK mechanism.?
?
In TCP there is an advanced error checking, but in UDP there is a basic error checking mechanism.?
?
Both TCP and UDP has headers but TCP has longer header. A UDP header is 8 bytes long while TCP header is 20 bytes long.?
?
Different applications uses these protocols by default. For example, DNS, FTP, HTTPS use TCP ports, while DHCP, SNMP, TFTP use UDP ports.?
________________________________________
Last Word
Here, we have compared TCP and UDP protocols. We have explained the key features of these transport layer protocols of OSI Reference Model.?
________________________________________
For More, You Can Also Visit www.ipcisco.com
??? Engineer & Manufacturer ?? | Internet Bonding routers to Video Servers | Network equipment production | ISP Independent IP address provider | Customized Packet level Encryption & Security ?? | On-premises Cloud ?
1 年Very interesting post! The distinctions between TCP and UDP are often overlooked, but it's clear that you understand the importance of the differences in how they operate. It's worth noting that TCP is a connection-oriented protocol, while UDP is connectionless. This means that TCP requires a connection to be established before data is sent, and UDP can send data without a connection being established. Additionally, TCP has error recovery and retransmission abilities, while UDP does not. It's fascinating how these protocols are used in so many different ways. You talked about the importance of TCP and UDP in your post. In what scenarios would you recommend using one protocol versus the other, especially in cases where there is a need for reliable data transmissions?
Sicher digitalisieren - Für Menschen und Unternehmen
1 年TCP is not secure, it is just as insecure as UDP. I'm sure what you really mean is that TCP is "reliable".