OWASP Top 10 API Security Risks – 2023
ABHAY CHAUDHARY
Immediate Joiner | Engineering Manager | AWS | Node.js | Dynamodb || MySQL | MongoDB | Redis | Test-Driven Development (TDD) | Software Development | Agile | Git | Educator
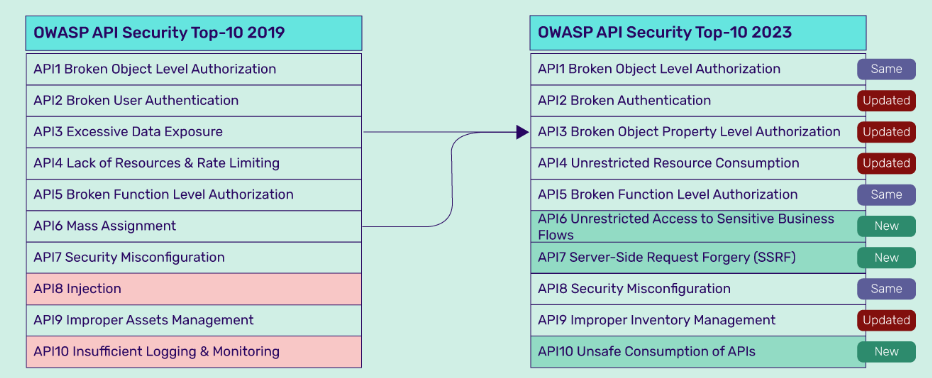
1. Broken Object Level Authorization
2. Broken Authentication
3. Broken Object Property Level Authorization
4. Unrestricted Resource Consumption
5. Broken Function Level Authorization
6. Unrestricted Access to Sensitive Business Flows
7. Server Side Request Forgery (SSRF)
领英推荐
8. Security Misconfiguration
9. Improper Inventory Management
10. Unsafe Consumption of APIs
For more details, you can refer to the original https://owasp.org/API-Security/editions/2023/en/0x11-t10/ OWASP? Foundation
Beyond the Top 10
#Injections
#Insufficient #Logging & #Monitoring
Business Logic Flaws
IT Certification at TIBCO
1 年Exciting news for F5 Certification aspirants! ?? www.certfun.com/f5 offers top-tier online practice exams. #CertFun #F5 #TechSkills