The NIST Cybersecurity Framework (CSF) is a voluntary set of standards, guidelines, and best practices to help organizations manage cybersecurity risk. It was first published in 2014 by the National Institute of Standards and Technology (NIST), a federal agency within the U.S. Department of Commerce. Since then, the CSF has been widely adopted by various sectors, industries, and countries as a common language and approach for cybersecurity.
However, the cybersecurity landscape is constantly evolving, and so is the CSF. In 2018, NIST released the CSF version 1.1, which introduced some minor updates and clarifications to the original version. In 2023, NIST is expected to release the CSF version 2.0, which will include some significant changes and enhancements to the framework. In this article, we will explore what's new in the CSF 2.0, and how it compares to another popular cybersecurity model: the zero trust security model.
What's New in the CSF 2.0?
According to NIST, the CSF 2.0 is intended to "Reflect the current state of cybersecurity and the evolving needs of the CSF community." Some of the main objectives of the CSF 2.0 are to:
- Align the CSF with other relevant standards and frameworks, such as the NIST Privacy Framework, the NIST Risk Management Framework, and the ISO/IEC 27000 series.
- Incorporate new and emerging topics and technologies, such as cloud computing, Internet of Things (IoT), artificial intelligence (AI), and 5G.
- Enhance the usability and applicability of the CSF across different contexts and environments, such as small and medium-sized businesses, critical infrastructure, and international settings.
- Provide more guidance and examples for implementing and measuring the CSF, such as maturity models, metrics, and case studies.
To achieve these objectives, NIST has proposed several changes and additions to the CSF 2.0, which are currently under public review and comment. Some of the most notable ones are:
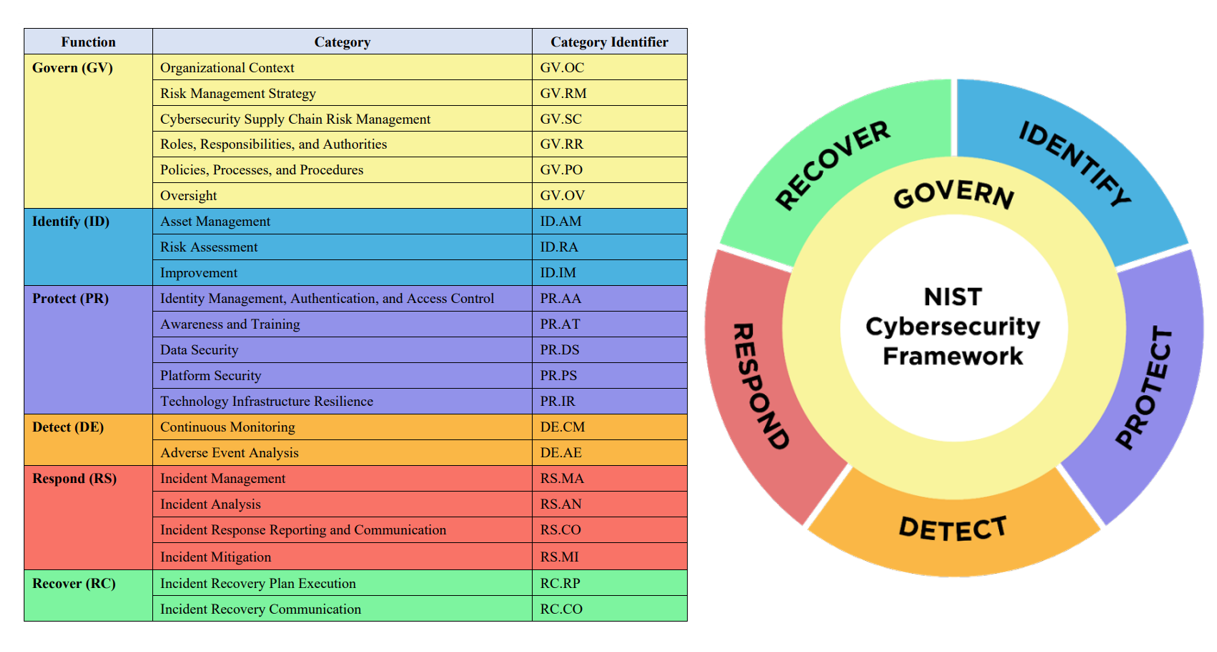
- A new structure for the CSF Core, which is the main component of the framework that consists of five Functions, 23 Categories, and 108 Subcategories. The new structure aims to simplify and streamline the Core, as well as to align it with the NIST Privacy Framework. The new Core will have four Functions (Identify, Protect, Respond, and Recover), 18 Categories, and 72 Subcategories. The Detect Function will be integrated into the other Functions, and some Categories and Subcategories will be merged, renamed, or removed.
- A new element for the CSF Core, called Implementation Examples, which will provide concrete and illustrative examples of how to apply the Subcategories in different scenarios and domains. The Implementation Examples will be based on existing standards, guidelines, and best practices from various sources, such as NIST, ISO, CIS, and others. The Implementation Examples will also be mapped to the corresponding Informative References, which are the existing standards and guidelines that support the Subcategories.
- A new element for the CSF Implementation Tiers, which are the levels of rigor and sophistication in applying the CSF. The new element, called Tier Attributes, will describe the characteristics and outcomes of each Tier, such as risk management processes, governance structures, resources, and capabilities. The Tier Attributes will help organizations assess their current and desired Tiers, as well as to communicate and compare their Tiers with other stakeholders.
- A new section for the CSF Profile, which is the representation of the outcomes that an organization has selected from the CSF Core based on its business needs and risk appetite. The new section, called Profile Prioritization, will provide guidance and methods for prioritizing the Subcategories within a Profile, such as using a scoring system, a ranking system, or a heat map. The Profile Prioritization will help organizations allocate their resources and efforts more effectively and efficiently.
How Does the CSF 2.0 Compare to Zero Trust?
The Zero Trust security model is another approach to cybersecurity that has gained popularity in recent years. The Zero Trust model is based on the principle of "Never Trust, Always Verify", which means that no user, device, or request should be trusted by default, regardless of whether they are inside or outside the network perimeter. Instead, every access request should be verified based on multiple factors, such as identity, location, device health, data sensitivity, and anomaly detection. The zero trust model also advocates for the use of least-privilege access, end-to-end encryption, and continuous monitoring and improvement.
The CSF 2.0 and the zero trust model are not mutually exclusive, but rather complementary and compatible. The CSF 2.0 provides a flexible and adaptable framework that can accommodate different cybersecurity models and strategies, including zero trust. In fact, some of the proposed changes and additions to the CSF 2.0 are aligned with the zero trust principles, such as:
- The new structure for the CSF Core, which emphasizes the importance of identifying and protecting the data, assets, and services that are most critical and valuable for the organization, as well as responding and recovering from incidents that may affect them. This is consistent with the zero trust concept of defining and securing the protect surface, which is the collection of data, applications, assets, and services that support the organization's mission and goals.
- The new element for the CSF Core, called Implementation Examples, which will include examples of how to implement Zero Trust architectures and practices, such as using micro-segmentation, multi-factor authentication, device compliance, and risk-based policies. These examples will help organizations adopt and apply the zero trust model in their specific contexts and environments.
- The new element for the CSF Implementation Tiers, called Tier Attributes, which will describe the level of maturity and sophistication of the organization's cybersecurity capabilities and processes. The Tier Attributes will help organizations assess their current and desired state of zero trust implementation, as well as to communicate and compare their progress and performance with other stakeholders.
- The new section for the CSF Profile, called Profile Prioritization, which will provide guidance and methods for prioritizing the Subcategories within a Profile, based on the organization's risk appetite and business needs. The Profile Prioritization will help organizations focus on the most important and impactful outcomes for achieving zero trust, as well as to allocate their resources and efforts more efficiently and effectively.
What are the benefits and advantages of the CSF 2.0?
The CSF 2.0 is expected to bring several benefits and advantages to the CSF users and stakeholders, such as:
- Enhancing the alignment and integration of cybersecurity risk management with enterprise risk management and governance, thereby increasing the visibility and accountability of cybersecurity at the senior leadership level and fostering a culture of cybersecurity across the organization.
- Addressing the growing and evolving cybersecurity challenges and opportunities posed by the global and complex supply chain ecosystem, thereby improving the security and resilience of the organization and its products, services and information.
- Providing more guidance and support for the implementation of the Framework Core, thereby facilitating the adoption and use of the CSF and enhancing the effectiveness and efficiency of the cybersecurity risk management processes and practices.
- Offering more flexibility and customization for the creation and communication of the Framework Profiles, thereby enabling the organization to tailor its cybersecurity risk management to its specific needs, goals and context.
- Increasing the awareness and understanding of the CSF and its value proposition, thereby promoting the adoption and use of the CSF and fostering a common language and approach for cybersecurity risk management among different sectors and regions.
Conclusion
The NIST Cybersecurity Framework 2.0 is a major update to the existing framework that aims to reflect the current state of cybersecurity and the evolving needs of the CSF community. The CSF 2.0 will introduce several changes and additions to the framework, such as a new structure for the CSF Core, a new element for the CSF Core called Implementation Examples, a new element for the CSF Implementation Tiers called Tier Attributes, and a new section for the CSF Profile called Profile Prioritization. These changes and additions will enhance the usability and applicability of the CSF across different contexts and environments, as well as to align it with other relevant standards and frameworks.
The CSF 2.0 and the Zero Trust security model are not mutually exclusive, but rather complementary and compatible. The CSF 2.0 provides a flexible and adaptable framework that can accommodate different cybersecurity models and strategies, including Zero Trust. Some of the proposed changes and additions to the CSF 2.0 are aligned with the Zero Trust principles, such as identifying and protecting the protect surface, verifying every access request, using least-privilege access and encryption, and assuming breach. The CSF 2.0 will also provide guidance and examples for implementing and measuring the zero trust model, as well as for prioritizing and communicating the Zero Trust outcomes.
The CSF 2.0 is currently under public review and comment, and NIST welcomes feedback from the CSF community and other interested parties. The final version of the CSF 2.0 is expected to be released in 2023. For more information and updates on the CSF 2.0, please visit the NIST website
.
Program Manager | PMP | Ex-CITRIX, Ex-DELL | KPMG -FLP |
2 个月Is this the latest one?
Senior Information Security Professional
3 个月Thank you for the article; it’s really helpful. I have a question regarding the scoring: If a category or subcategory is not applicable, how should it be scored? Does this affect the overall score, or does the tool not provide an option for marking items as not applicable?
Experienced MD/CEO | Banking, Finance, HRM, Coaching, Leadership, Corporate Governance, Compliance, Change and Strategic Management, Team Building.
1 年Dear Lahiru, Very important article. Much useful for my studies these days. Greatly appreciate.