Microsoft Entra ID Exploit: Privilege Escalation via Abandoned Reply URL
Introduction:
A privilege escalation exploit related to Microsoft Entra ID (formerly Azure Active Directory) service has been discovered by Secureworks Counter Threat Unit researchers. This exploit revolves around an abandoned reply URL, allowing attackers to manipulate authorization codes, access tokens, and gain elevated privileges. Microsoft promptly addressed the issue with an update soon after responsible disclosure on April 5, 2023.
Exploit Mechanics:
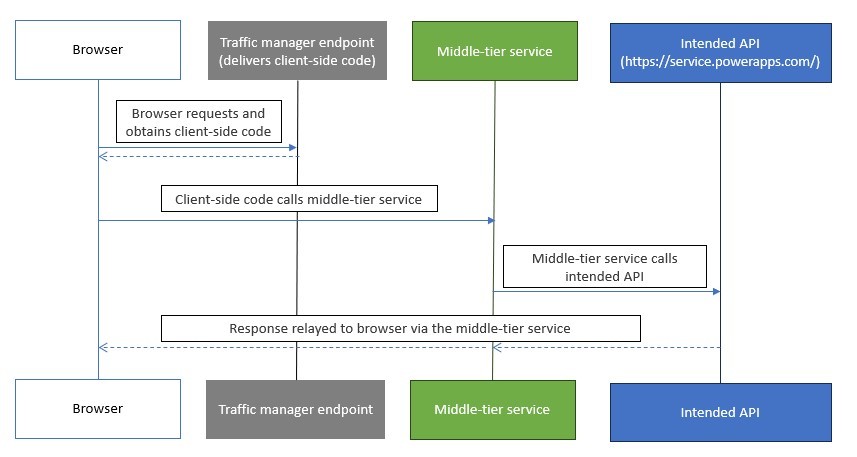
Attackers could exploit a defunct reply URL to reroute authorization codes, replacing them with unauthorized codes for access tokens. These manipulated tokens were then used to access the Power Platform API through a middle-tier service, granting them enhanced privileges. The reply URL, which serves as the destination for authorization server responses, was compromised to transmit unauthorized codes, enabling attackers to perform unauthorized actions.
Resolution and Mitigation:
Microsoft's quick action rectified the vulnerability via an update, which was delivered within a day of the responsible disclosure. Secureworks CTU has introduced an open-source application that other organizations can utilize to detect abandoned reply URLs. Microsoft emphasizes the importance of accurately registering redirect URLs during app registration to ensure secure authorization code and token delivery.
Potential Impact:
In a hypothetical attack scenario, attackers could manipulate abandoned reply URLs linked with Azure Traffic Manager profiles, allowing a middle-tier service to access the Power Platform API and control environment parameters. This could lead to acquiring system administrator roles and carrying out various malicious actions. Such actions could be initiated when victims click on malicious links that compromise the redirect URL and transmit unauthorized authorization codes.
领英推荐
Related Threat:
Another investigation by Kroll revealed a DocuSign-themed phishing campaign using open redirects. Attackers spread specially crafted URLs through phishing emails, redirecting victims to malicious websites upon clicking, illustrating the risk associated with open redirect vulnerabilities.
References:
Countermeasures:
To safeguard against this evolving threat landscape, the following measures are recommended:
Stay vigilant and adhere to these guidelines to ensure the protection of your systems.
Stay Secure.