Cybersecurity threats have become a pressing issue as the world grows increasingly digital. Every day, individuals and businesses face risks from malicious software designed to steal data, cause disruptions, and hold systems hostage. Two of the most significant threats in this domain are malware and ransomware. While both fall under the same general category of harmful software, they have distinct purposes and methods of attack. Understanding the differences between malware and ransomware is essential to effectively protect yourself and your organization.
What Is Malware?
Malware
, short for “malicious software,” refers to any software intentionally created to damage or disrupt computers, systems, or networks. Malware has various forms and can serve different purposes, from stealing sensitive information to crippling systems. Common types of malware include viruses, worms, trojans, spyware, and adware.
- Viruses:?A virus is designed to infect other legitimate files or programs. Once the virus is activated, it can spread, causing harm such as deleting files, slowing down performance, or crashing the system.
Example: Downloading a document attached to an email from an unknown sender can cause the virus to infect the system by corrupting important files or attaching itself to other programs.
- Trojans:?A trojan disguises itself as a legitimate application or file to trick users into installing it. Once installed, it allows attackers to access the system remotely, steal data, or introduce additional malware.
Example: A free game download from an unofficial website could be a trojan that silently installs malware, enabling hackers to steal sensitive information like bank details.
- Spyware:?Spyware is software that secretly monitors a user’s activities and sends this information to a third party. It can track keystrokes, take screenshots, or even activate your webcam.
Example: Spyware could track your online activities to gather login credentials, allowing attackers to access your online accounts.
- Worms:?Worms are self-replicating malware that can spread without human interaction, exploiting vulnerabilities in networks to infect multiple devices quickly.
Example: A worm spreads through a company’s network, causing widespread system crashes and data loss across multiple devices.
- Adware:?Adware shows unwanted advertisements, usually as pop-ups, which can slow down devices and bombard users with invasive ads.
Example: After installing a free software bundled with adware, users may experience continuous pop-up ads that could lead to more dangerous types of malware.
- Cryptojacking:?Cryptojacking involves secretly using your computer’s resources to mine cryptocurrency without your consent, which can slow down your device significantly.
Example: A compromised website injects cryptojacking malware into your browser, using your system to mine cryptocurrency, making your computer sluggish.
What Is Ransomware?
Ransomware
is a specific type of malware designed to block access to data or entire systems until a ransom is paid to the attacker. The primary objective of ransomware is financial extortion.
- Infection: Delivered via phishing emails, malicious downloads, or infected websites.
- Encryption: Encrypts the victim’s data, making it impossible to access.
- Ransom Demand: Displays a ransom demand, often in cryptocurrency, to unlock the files.
- Decryption: If paid, the attacker may provide a decryption key, though it’s not guaranteed.
Practical Example of Ransomware Attack
In 2017, the WannaCry ransomware attack affected over 200,000 computers in 150 countries. WannaCry exploited a vulnerability in Microsoft Windows, encrypting files on infected systems. Victims were locked out of their data and had to pay a ransom in Bitcoin. This attack severely impacted hospitals, businesses, and government agencies. In some cases, paying the ransom didn’t guarantee the recovery of data, leading to significant financial losses and operational disruptions.
How Ransomware Spreads
- Phishing Emails:?An employee receives an email that looks like it’s from a trusted source, like a delivery service or a bank. The email contains an attachment that, when opened, installs ransomware on the system. Once installed, the ransomware encrypts the files and displays a ransom demand.
- Malicious Advertising (Malvertising):?While browsing the web, a user clicks on what seems to be a legitimate advertisement. However, this ad contains hidden malicious code that installs ransomware on their device, locking them out of their data.
- Infected Software:?Users looking to save money may download a pirated version of an expensive software application. Unknown to them, this pirated version contains ransomware that will encrypt their files once the software is executed.
- Remote Desktop Protocol (RDP) Exploits:?Many organizations use RDP to allow employees to remotely access their systems. If the RDP is improperly configured or secured with a weak password, attackers can break in and install ransomware, taking control of the entire system.
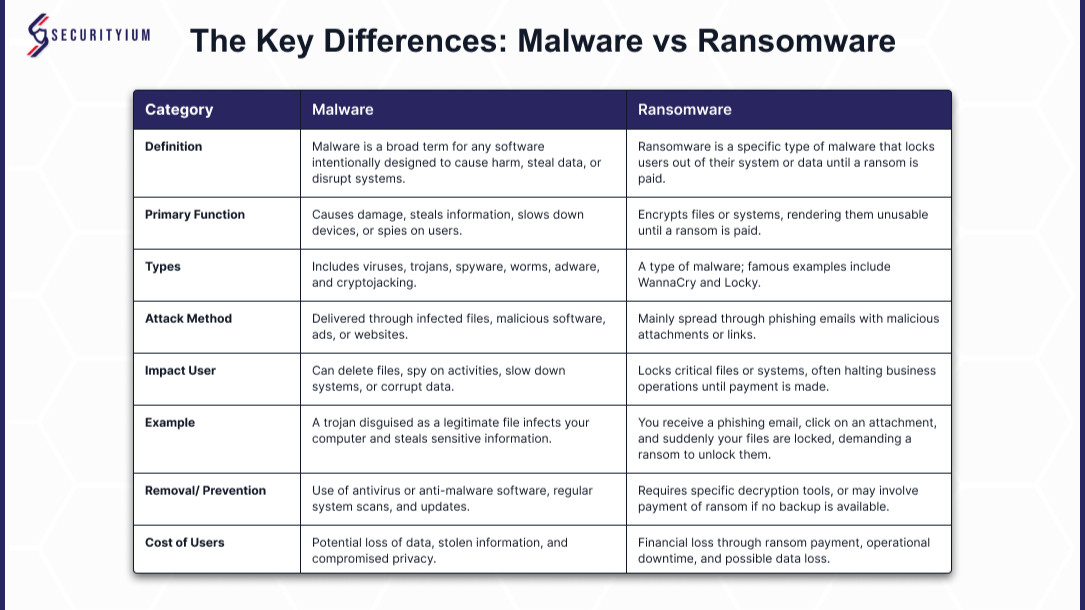
Key Differences Between Malware and Ransomware
Although ransomware is a type of malware, they differ in terms of purpose, methods of attack, and impact. Understanding these distinctions is crucial for implementing the correct cybersecurity strategies.
1. Purpose
- Malware: Malware’s primary goal is to disrupt, damage, or gain unauthorized access to a system. Malware can be used for a wide variety of purposes, from spying on a user’s activities to stealing sensitive information. Example: Spyware secretly tracks your online activities to gather your personal information, such as credit card numbers, for identity theft.
- Ransomware: The purpose of ransomware is financial extortion. It locks a system or encrypts data and demands a ransom for the release of that information. Example: A business gets hit with ransomware, and all its critical data becomes inaccessible. The attacker demands payment in cryptocurrency in exchange for the decryption key to unlock the data.
2. Method of Attack
- Malware: Malware can infect a system through malicious downloads, infected files, and software vulnerabilities. It may spread automatically or require user interaction. Example: A virus may spread by attaching itself to commonly shared files or documents, infecting multiple users within a network.
- Ransomware: Ransomware usually spreads through phishing emails, malicious links, or software vulnerabilities. Once inside the system, it encrypts data, locking the user out. Example: A user clicks on a seemingly legitimate email attachment, installing ransomware that encrypts their entire system, and demands a ransom to unlock it.
3. Impact on Systems
- Malware: Malware can slow down systems, delete files, or provide unauthorized access to attackers. The effects can range from minor inconvenience to complete system failure. Example: A worm spreads across a network, deleting important files and causing system crashes across multiple devices.
- Ransomware: Ransomware has a more immediate and visible impact, locking users out of their files until a ransom is paid. It doesn’t typically destroy data but makes it inaccessible. Example: A company’s financial data becomes encrypted due to a ransomware attack, rendering it unusable for business operations until the ransom is paid.
How to Prevent Malware and Ransomware Attacks
Both malware and ransomware pose serious threats but following good cybersecurity practices can reduce your risk significantly. Below are some practical tips for prevention.
- Keep Your Operating System and Software Up to Date:?Updating your system regularly ensures that vulnerabilities in the software are patched, reducing the risk of exploitation by malware or ransomware. Example: If your company uses an outdated operating system like Windows XP, it becomes an easy target for attackers exploiting known vulnerabilities. Regular updates help close these security gaps.
- Use Strong, Unique Passwords:?Using strong passwords reduces the risk of attackers guessing or cracking your login credentials. Passwords should be at least 16 characters long and include letters, numbers, and special characters. Example: An employee using “password123” as their login credential is much more vulnerable than one using a complex password generated by a password manager.
- Enable Multi-Factor Authentication (MFA):?Multi-factor authentication adds an extra layer of security by requiring a second form of verification, such as a text message code, in addition to your password. Example: Even if an attacker manages to steal your password, they still won’t be able to access your account without the second verification step, reducing the risk of unauthorized access.
- Be Wary of Phishing Emails and Malicious Links:?Always verify the authenticity of emails, attachments, and links before interacting with them. Example: An employee receives an email claiming to be from IT, asking them to click a link to update their login information. By carefully inspecting the email’s sender and scanning the link using a tool like Google Transparency Report, the employee can avoid a potential phishing scam.
- Backup Data Regularly:?Regularly backing up data ensures that, even in the event of a ransomware attack, you can restore your files without having to pay the ransom. Example: If ransomware locks your files, you can restore them from a cloud-based backup and avoid paying the ransom, minimizing downtime and financial loss.
- Educate Employees About Cybersecurity:?Employees are often the first line of defense against cyberattacks. Regular training helps them recognize phishing scams, suspicious attachments, and other potential threats. Example: A company could hold regular cybersecurity workshops, teaching employees how to spot phishing emails and avoid clicking on suspicious links. This proactive approach can prevent ransomware from spreading within the organization.
Conclusion
While malware and ransomware are both serious cybersecurity threats, understanding their differences allows for better protection strategies. Malware refers to a broad category of malicious software with various purposes, while ransomware specifically focuses on extorting money by holding data hostage. Implementing robust cybersecurity measures—such as keeping software updated, using strong passwords, and regularly backing up data—can significantly reduce the risks associated with both malware and ransomware. Taking a proactive approach to cybersecurity will help individuals and organizations safeguard their systems and avoid the damaging effects of cyberattacks.