Incident Response: A Comprehensive Guide to Handling Security Issues
Incident response deals with the entire lifecycle of an incident from start to finish. It involves proactive measures to prevent incidents, reactive steps to address them when they occur, and strategies to mitigate their impact. This guide ensures you are well prepared to deal with various security challenges.
So, what are incidents?
Several processes run on your devices. Some are interactive, like watching videos or playing games. Others are non-interactive and run in the background and don’t need you to do anything.
Every action creates events, which are recorded. And these devices generate tons of events because many tasks happen at once. Some of these events can indicate something wrong.
To check for issues among this mountain of events, we use security solutions. They collect logs of these events and help spot any harmful activity.
True vs False Positive
When security systems flag potential issues, they can be categorized as:
False Positive: A security system alerted on a lot of data going from one system to an outside IP. The security team checked it out and found it was just a backup to cloud storage. That’s a false positive.
True Positive: A security system flagged a phishing email aimed at one of the users. The team looked into it and confirmed it was indeed a phishing attempt. That’s a true positive.
Types of Security Incidents:
There are different types of incidents that can happen alone or together.
Malware Infections:
Malware is malicious software that can harm systems, networks, or applications. It's the most common type of security incident and can spread through various file types, including text, documents, and executables
Security Breaches:
Security breaches happen when someone gains unauthorized access to private data. This is serious for businesses since they need to keep this data safe for their authorized users.
Data Leaks:
Data leaks occur when private information is exposed by accident or by attackers. These leaks can harm an organization’s reputation or be used to threaten victims. Unlike breaches, they can happen because of human mistakes or poor config setups.
Insider Attacks:
Insider Attacks come from within an organization, like a disgruntled employee infecting the network on their last day. These attacks are risky since insiders usually have greater access to sensitive information.
Denial Of Service Attacks:
Denial of Service Attacks (DoS) aim to make a system unavailable by overwhelming it with fake requests. This can block legitimate users from accessing crucial data.
Each of these incidents can severely impact victims, but the effect varies. What hurts one organization might not be as damaging to another.
Incident Response Lifecycle:
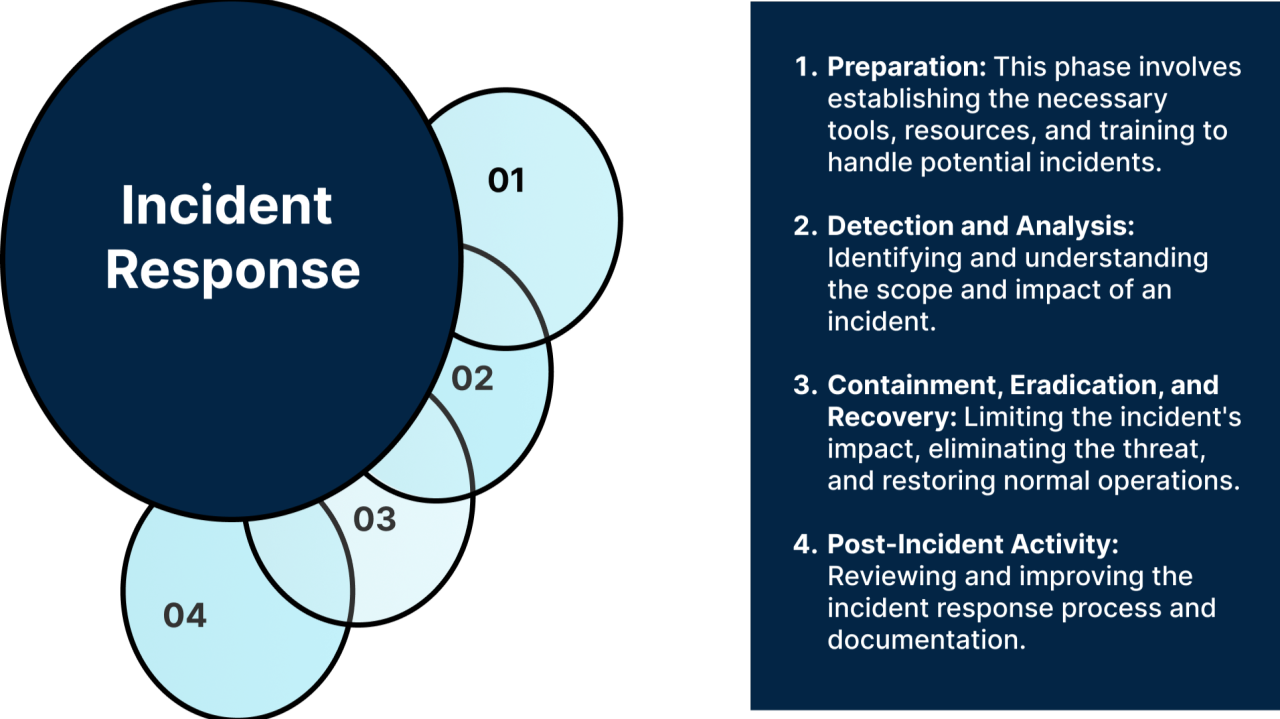
The NIST Incident Response framework involves four steps:
Incident Response Mindset:
When thrust into an emergency, the urgency and pressure to find a solution can make it easy to lose sight of the bigger picture.
One of the key objectives of the incident response cycle is to provide valuable insights for future incidents. This makes it essential to document every action taken and every piece of information gathered. As incident responders, we have a dual responsibility: not only to eliminate the immediate threat but also to ensure it does not pose a risk to our organization again.