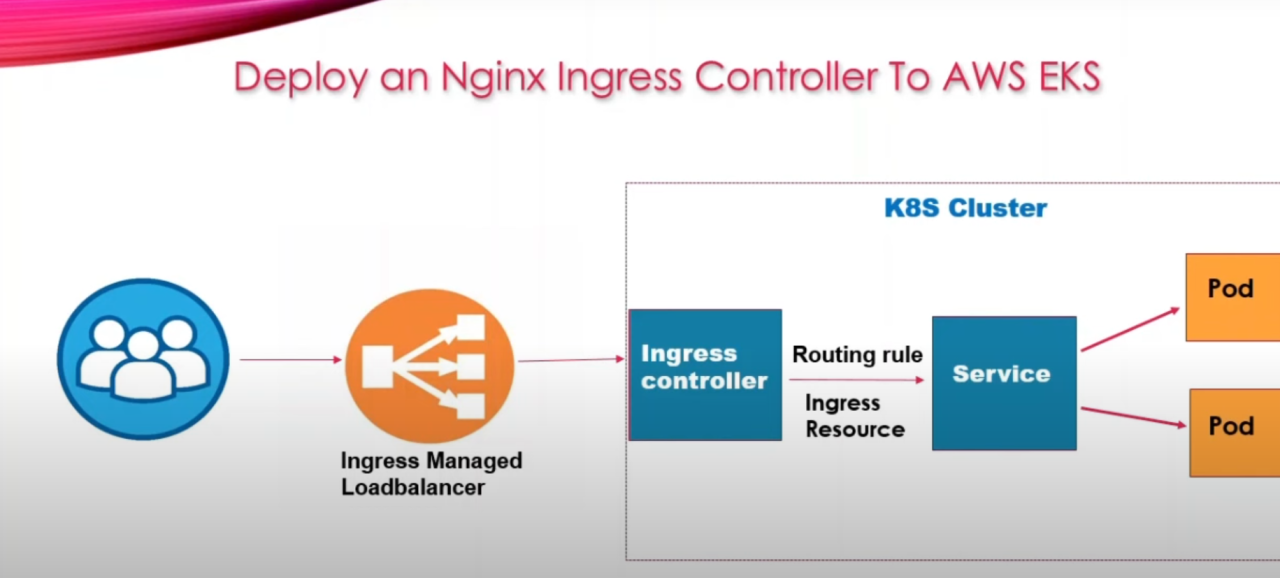
How to Deploy An Nginx Ingress Controller in AWS EKS along with SSL termination in EKS.
Ramandeep Chandna
System Engineering Manager AWS | 7xAWS | CKA | CKAD | 2xCloudBees
Use case using the STAR (Situation, Task, Action, Result) method to switch SSL termination from an AWS Application Load Balancer (ALB) to an SSL termination within an EKS cluster using an Nginx Ingress Controller.
Situation
You are currently using an AWS Application Load Balancer (ALB) to terminate SSL/TLS traffic for your applications running on AWS Elastic Kubernetes Service (EKS). This setup works well, but you want to switch to using SSL termination in your EKS cluster with the Nginx Ingress Controller for better control, flexibility, and potentially reduced costs.
Task
The task is to configure SSL termination within the EKS cluster
Actions
1. Setting up Nginx Ingress Controller in EKS
Assuming you have Flux and Terraform set up, let's start with deploying the Nginx Ingress Controller.
Terraform Configuration:
Create a Terraform file nginx-ingress.tf
provider "kubernetes" {
config_path = "~/.kube/config"
}
resource "helm_release" "nginx_ingress" {
name = "nginx-ingress"
repository = "https://kubernetes.github.io/ingress-nginx"
chart = "ingress-nginx"
version = "4.0.1"
set {
name = "controller.service.type"
value = "LoadBalancer"
}
set {
name = "controller.service.externalTrafficPolicy"
value = "Local"
}
}
Apply the Terraform configuration:
terraform init
terraform apply -auto-approve
2. Converting a .pfx File to Generate cert.pem and key.pem Files
Use OpenSSL to convert the .pfx file to cert.pem and key.pem.
openssl pkcs12 -in your-cert.pfx -out cert.pem -clcerts -nokeys
openssl pkcs12 -in your-cert.pfx -out key.pem -nocerts -nodes
3. Creating a Kubernetes Secret for SSL Certificate
Create a Kubernetes Secret to store the SSL certificate and key
kubectl create secret tls my-tls-secret --cert=cert.pem --key=key.pem -n your-namespace
4. Modifying the Ingress Resource
Create the Kubernetes Ingress resource with secret to connect to ingress controller using terraform script , Also create Service Type Cluster IP for service to communicate to application pods.
Create a file named ingress.yaml:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: my-app-ingress
namespace: your-namespace
annotations:
nginx.ingress.kubernetes.io/ssl-redirect: "true"
nginx.ingress.kubernetes.io/force-ssl-redirect: "true"
nginx.ingress.kubernetes.io/rewrite-target: /
spec:
ingressClassName: nginx
领英推荐
tls:
- hosts:
- my-app.example.com
secretName: my-tls-secret
rules:
- host: my-app.example.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: my-app-service
port:
number: 80
---
apiVersion: v1
kind: Service
metadata:
name: my-app-service
namespace: your-namespace
spec:
type: ClusterIP
selector:
app: my-app
ports:
- port: 80
targetPort: 7007
protocol: TCP
name: http
5. Updating Flux
Prerequisite: Flux is already configured for your EKS cluster.
Ensure your GitOps setup is properly configured to handle these changes. Commit and push the ingress.yaml file to your Git repository to trigger the Flux deployment.
Apply manifest
kubectl apply -f ingress.yaml
6. Configuring the AWS Application Load Balancer
Ingress Managed Application Load Balancer is by default deployed as part of nginx-ingress controller deployment .Earlier Application pods were directly communicating to Service Type Load balancer to route traffic from application load balancer to pod. Now in place of Application load balancer application will pointing to Service Type Cluster IP.
Cluster IP service will be routing traffic to Ingress controller using Ingress Resource rules. SSL certificate rules are defined in ingress resources. So Ingress Managed Application Load Balancer will pass the traffic to ingress controller to process with SSL termination in EKS cluster.
Result
With these steps completed, SSL termination is now handled by the Nginx Ingress Controller within your EKS cluster. The ALB passes traffic to the Nginx Ingress Controller, which terminates the SSL connection. This offers better control over SSL/TLS configurations, potentially lowers costs by reducing reliance on AWS ALB for SSL termination, and provides more flexibility in managing SSL certificates.
Benefits of Moving SSL Termination to Ingress Controller
Conclusion
Moving SSL termination to the Nginx Ingress Controller within your EKS cluster provides several significant benefits, including cost savings, enhanced control and security, simplified certificate management, and improved performance. By leveraging the flexibility and powerful features of Nginx Ingress, you can achieve a more efficient, secure, and manageable setup for handling SSL/TLS traffic in your Kubernetes environment.
Resources :
?? Explore my Digital Product AWS DevSecOps industry wide use cases: https://lnkd.in/dzUGDBwY
?? Join the AWS DevSecOps Community: https://lnkd.in/dDsf4rCv
?? Subscribe to the Newsletter: https://lnkd.in/gqgkFZCp
?? Follow on LinkedIn: https://lnkd.in/gy8xy2Gb
?? Subscribe to the YouTube Channel: https://lnkd.in/g6mSHukf
Remember to like, share, and comment to help spread valuable knowledge further. Let's keep learning and growing together.
def will read
System Engineer - DevOps Professional @Infosys | AWS Certified Developer Associate | 2x Azure | Python | Docker | Kubernetes | Terraform | AWS | Jenkins | HELM | ASL | Shell Scripting | GitOps | Jira
4 个月Great article! Ramandeep Chandna Deploying the NGINX Ingress Controller on AWS EKS with SSL is crucial for secure and efficient traffic management. Your step-by-step guide is incredibly helpful, especially the detailed instructions on SSL setup. This will be a valuable resource for anyone looking to enhance their Kubernetes environment with robust ingress capabilities. Thanks for sharing!