How to Automate Your Attack Surface Management
In the evolving landscape of cybersecurity, the concept of Attack Surface Management (ASM) has become crucial. As organizations increasingly rely on digital assets, their attack surface—the sum of all potential entry points where an attacker can infiltrate—continues to expand. Managing this attack surface effectively is critical to protecting sensitive data, maintaining customer trust, and ensuring business continuity. However, traditional methods of ASM can be labor-intensive and prone to human error. The solution? Automating your Attack Surface Management.
This blog will explore the importance of ASM, the challenges of manual management, and how automation can streamline and enhance your security efforts. By the end, you'll understand how to implement automated ASM in your organization and the benefits it can bring.
Understanding Attack Surface Management (ASM)
What is Attack Surface Management?
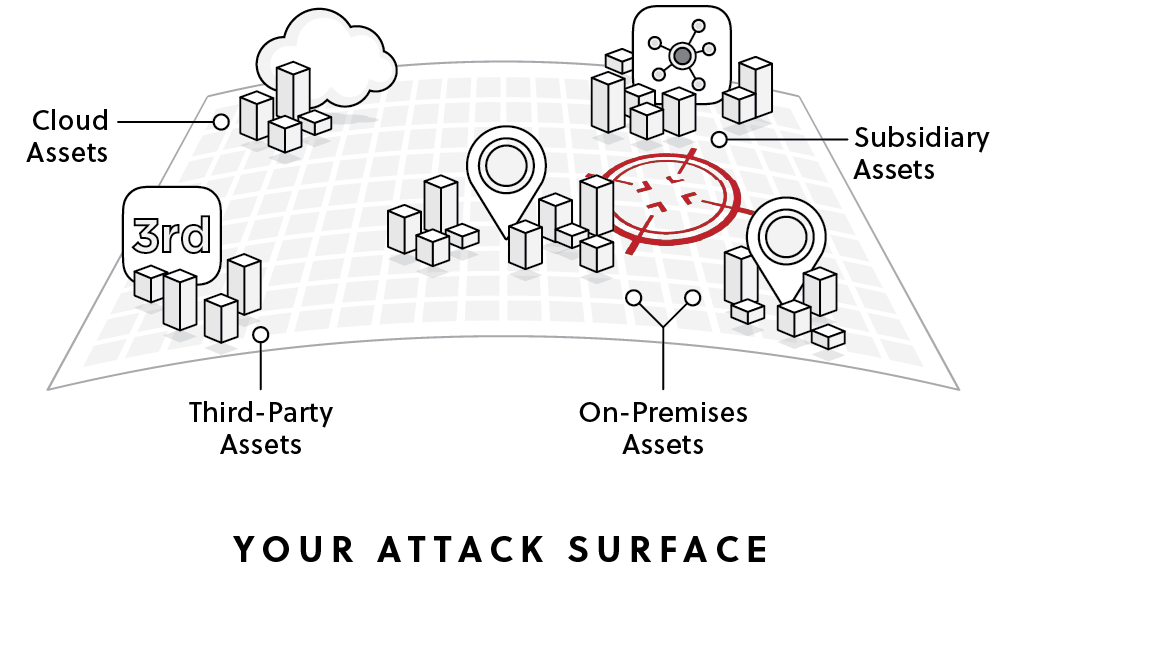
Attack Surface Management is the continuous process of discovering, analyzing, and mitigating potential vulnerabilities across an organization's entire digital footprint. This includes not just the publicly exposed assets but also the internal systems, shadow IT, cloud services, and third-party integrations that could be exploited by malicious actors.
An attack surface comprises several elements, including:
Why is ASM Important?
As organizations grow, so does their digital footprint, which in turn increases their attack surface. Effective ASM is essential because it helps to:
Challenges of Manual Attack Surface Management
Before diving into automation, it's important to understand why traditional, manual ASM methods can fall short.
1. Complexity of Modern IT Environments
Today's IT environments are complex, with a mix of on-premises systems, cloud services, and hybrid infrastructures. Manually keeping track of all assets and potential vulnerabilities across these environments is nearly impossible.
2. Volume of Data
The sheer volume of data generated by modern IT systems can overwhelm security teams. Logs, alerts, and reports need to be analyzed in real-time to be effective, but manual processes are often too slow to keep up.
3. Human Error
Even the most skilled security professionals are prone to errors. Manual processes increase the likelihood of missed vulnerabilities, misconfigurations, and other mistakes that can leave an organization exposed.
4. Resource Intensive
Manual ASM is resource-intensive, requiring significant time and effort from security teams. This can lead to burnout and detract from other important security tasks.
5. Lack of Continuous Monitoring
Manual ASM processes are often periodic, meaning they only provide a snapshot of the attack surface at a specific time. In contrast, threats are constantly evolving, requiring continuous monitoring and assessment.
The Case for Automating Attack Surface Management
Given the challenges of manual ASM, automation emerges as a powerful solution. Automated ASM tools can provide continuous, real-time monitoring, reducing the burden on security teams and enhancing overall effectiveness.
1. Continuous and Real-Time Monitoring
Automated ASM tools provide continuous monitoring of the attack surface, ensuring that vulnerabilities are identified as soon as they arise. This real-time capability is crucial in a landscape where threats can evolve rapidly.
2. Comprehensive Asset Discovery
Automation allows for comprehensive discovery of all assets, including those that might be overlooked in manual processes. This includes shadow IT, cloud resources, and third-party integrations that could introduce vulnerabilities.
3. Prioritization of Risks
Automated tools can analyze vulnerabilities and prioritize them based on factors such as severity, exploitability, and impact on the business. This helps security teams focus their efforts on the most critical issues.
4. Reduced Human Error
By automating repetitive tasks, the risk of human error is significantly reduced. Automated ASM tools can consistently apply the same rules and logic, ensuring that vulnerabilities are not missed.
5. Scalability
As organizations grow, so does their attack surface. Automated ASM tools can scale to handle large and complex environments, providing the flexibility needed to adapt to changing needs.
6. Enhanced Incident Response
With automated ASM, security teams have access to real-time data and insights, allowing them to respond more quickly and effectively to incidents. This can significantly reduce the time to detect and remediate threats.
How to Automate Your Attack Surface Management
Automating ASM involves several steps, from selecting the right tools to integrating them into your existing security infrastructure. Here’s a step-by-step guide to help you get started.
Step 1: Assess Your Current Attack Surface
Before you can automate ASM, you need a clear understanding of your current attack surface. This involves:
Step 2: Choose the Right ASM Tools
There are several automated ASM tools available, each with its strengths and features. When selecting a tool, consider the following:
Popular automated ASM tools include:
领英推荐
Step 3: Integrate ASM Tools with Existing Security Infrastructure
To maximize the effectiveness of your automated ASM, integrate it with your existing security infrastructure. This can include:
Step 4: Automate Vulnerability Management
Once your ASM tools are in place, automate the vulnerability management process:
Step 5: Continuous Monitoring and Adaptation
Automation is not a set-it-and-forget-it solution. Continuous monitoring and adaptation are crucial to maintaining an effective ASM strategy:
Step 6: Educate and Train Your Team
Even with automation, your security team plays a critical role in ASM. Ensure that your team is well-trained on how to use the automated tools and understand the data and insights they provide. Continuous education and training will help your team stay up-to-date with the latest threats and security best practices.
Case Studies: Successful Implementation of Automated ASM
Case Study 1: Financial Services Company
A large financial services company with a complex IT environment implemented automated ASM to manage its extensive attack surface. By integrating RiskIQ with their SIEM system, they gained real-time visibility into their assets, including shadow IT and third-party integrations. The automation allowed them to prioritize risks based on business impact, leading to a 30% reduction in critical vulnerabilities within the first six months.
Case Study 2: Healthcare Organization
A healthcare organization dealing with sensitive patient data faced challenges in managing its attack surface manually. They adopted Tenable for automated vulnerability management and integrated it with their incident response platform. The automation streamlined their patch management process, reducing the time to remediate critical vulnerabilities from weeks to hours. This not only improved their security posture but also helped them meet stringent compliance requirements.
Case Study 3: E-commerce Platform
An e-commerce platform struggling with shadow IT and cloud sprawl turned to CyCognito for automated ASM. The tool helped them discover previously unknown assets and prioritize risks based on their exploitability. By automating their ASM processes, they achieved a 40% reduction in their attack surface within a year, significantly enhancing their security and reducing the risk of data breaches.
Best Practices for Automating Attack Surface Management
To maximize the benefits of automating ASM, follow these best practices:
How CloudMatos Helps in Automating Attack Surface Management
CloudMatos is a powerful cloud automation platform designed to streamline and enhance various aspects of cloud security, including Attack Surface Management (ASM). Here's how CloudMatos can help organizations automate and optimize their ASM processes:
1. Comprehensive Asset Discovery
CloudMatos excels in discovering and inventorying all assets across cloud environments. By automatically identifying cloud resources, including shadow IT and misconfigured assets, it ensures that organizations have a complete and up-to-date view of their attack surface. This capability is crucial in today's complex IT environments, where assets can be spun up or down quickly, often without proper oversight.
2. Continuous Monitoring and Real-Time Alerts
With CloudMatos, organizations can achieve continuous monitoring of their cloud environments. The platform provides real-time alerts on potential vulnerabilities, misconfigurations, and security risks, enabling security teams to respond swiftly to emerging threats. This continuous monitoring is vital for maintaining an accurate and current understanding of the attack surface.
3. Automated Compliance Management
CloudMatos helps organizations stay compliant with industry regulations by automating compliance checks and audits. The platform continuously monitors the cloud environment against predefined compliance frameworks (such as GDPR, HIPAA, or PCI-DSS) and automatically flags any non-compliant assets. This automation ensures that compliance requirements are met consistently, reducing the risk of regulatory fines and breaches.
4. Risk Prioritization and Remediation
CloudMatos not only identifies vulnerabilities but also prioritizes them based on factors such as severity, exploitability, and potential business impact. This helps security teams focus on the most critical issues first. Additionally, CloudMatos can automate remediation workflows, such as applying patches, reconfiguring security settings, or isolating vulnerable assets, thereby reducing the time to mitigate risks.
5. Integration with Existing Security Tools
CloudMatos integrates seamlessly with other security tools and platforms, such as SIEM systems, threat intelligence platforms, and incident response tools. This integration enhances the overall security ecosystem by ensuring that all aspects of ASM are interconnected and that data flows smoothly between systems, leading to more informed decision-making and faster incident response.
6. Scalability and Adaptability
As organizations grow and their cloud environments become more complex, CloudMatos scales to meet their needs. The platform can handle large-scale cloud infrastructures, providing the flexibility to adapt to changing business requirements and emerging threats. This scalability is essential for organizations looking to future-proof their ASM processes.
7. Automation of Routine Security Tasks
CloudMatos automates routine security tasks such as vulnerability scanning, patch management, and compliance checks. By automating these processes, CloudMatos reduces the burden on security teams, allowing them to focus on more strategic initiatives while minimizing the risk of human error.
8. Enhanced Incident Response
With CloudMatos, security teams have access to real-time data and insights that enhance their ability to respond to incidents. The platform's automation capabilities can trigger immediate responses to detected threats, such as isolating compromised resources or initiating a full-scale incident response procedure.
Here's the bar chart that illustrates the impact of various CloudMatos features on automating Attack Surface Management (ASM). Each feature is scored on a scale from 1 to 10 based on its importance and effectiveness in ASM.
?
Conclusion
CloudMatos provides a robust solution for automating Attack Surface Management, particularly in cloud environments. By leveraging its comprehensive asset discovery, continuous monitoring, automated compliance management, and seamless integration with existing security tools, organizations can significantly enhance their security posture. The platform's ability to automate routine tasks and prioritize risks ensures that security teams can respond more effectively to emerging threats, reducing the overall attack surface and improving resilience against cyberattacks.