HashiCorp Vault in Kubernetes: Secure Secrets Management for Modern Applications
Muhammed Safuvan K
DevOps Engineer | Expertise in OpenShift, Kubernetes, Docker, Jenkins, Azure DevOps, CI/CD Automation, GitOps, ArgoCD, CloudOps & Terraform
As organisations increasingly adopt Kubernetes (K8s) for container orchestration, managing and securing secrets becomes a critical challenge. Kubernetes natively stores secrets, but these are not encrypted by default and can be accessed with minimal restrictions. This is where HashiCorp Vault comes in—a powerful, flexible, and secure tool designed for advanced secret management and encryption as a service.
This article explores why HashiCorp Vault is essential for Kubernetes, detailing its key features, security benefits, and how it enhances Kubernetes security.
HashiCorp Vault
While Kubernetes Secrets provide basic secret storage, they have several limitations:
HashiCorp Vault solves these issues by providing:
Key Features of HashiCorp Vault in Kubernetes
1. Dynamic Secrets Management
Unlike traditional static secrets, dynamic secrets generated by Vault expire automatically and are unique per request.
Example: Instead of storing long-lived database credentials, Vault generates temporary credentials with an expiration time, ensuring security and reducing exposure.
2. Encryption as a Service
Vault allows applications running in Kubernetes to encrypt data without managing encryption keys manually.
Benefit: Applications can send data to Vault for encryption and decryption, ensuring sensitive information is never exposed in plaintext.
3. Granular Role-Based Access Control (RBAC)
Vault supports fine-grained access control using policies, allowing organisations to enforce the principle of least privilege.
Example: A Kubernetes pod requesting database credentials will receive only the necessary permissions for its specific role, rather than full database access.
4. Automatic Secret Rotation
Vault enables automatic rotation of secrets for databases, cloud credentials, and other sensitive information without downtime.
Example: If a Kubernetes workload requires AWS credentials, Vault can generate short-lived access keys that rotate automatically, improving security.
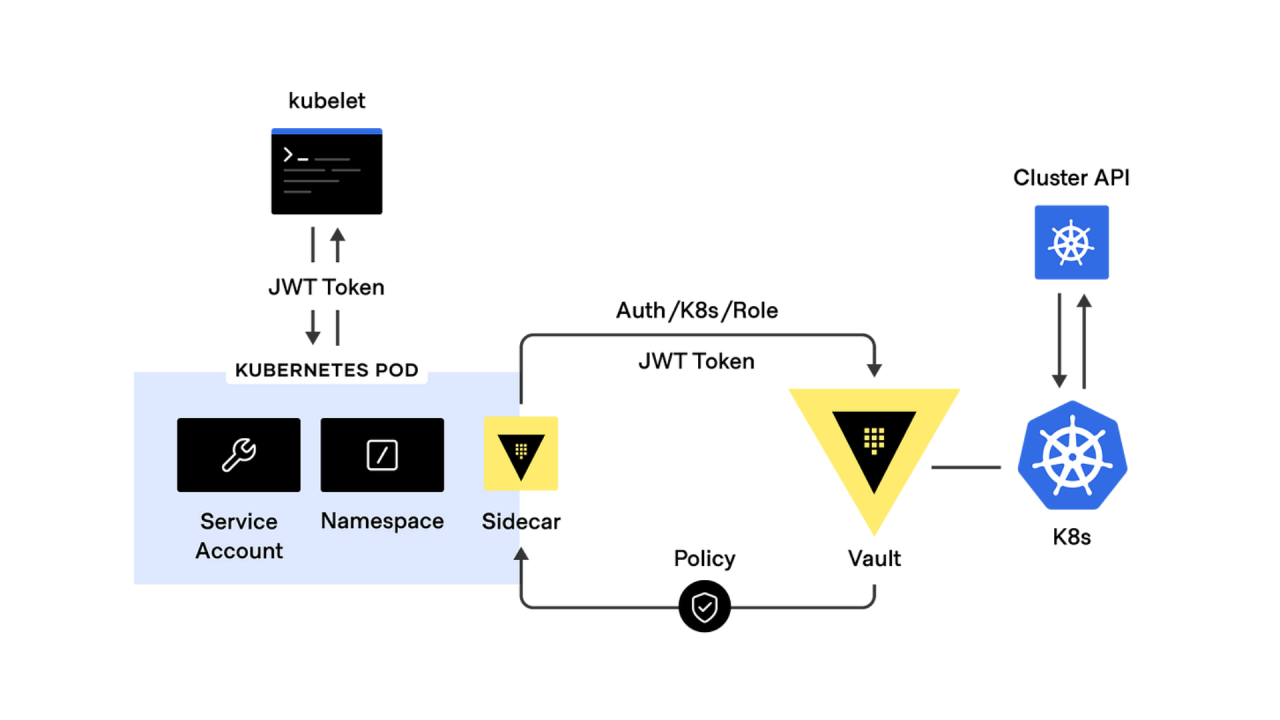
5. Secure Kubernetes Authentication
Vault provides a native Kubernetes authentication method, allowing workloads to authenticate securely using their Kubernetes ServiceAccount.
Benefit: Reduces the need for hardcoded credentials, as applications authenticate to Vault dynamically.
6. Audit Logging and Compliance
Vault records every request and action taken on secrets, providing a full audit trail for compliance and security monitoring.
Example: Security teams can track who accessed a secret, when, and for what purpose, reducing insider threats.
Benefits of Using HashiCorp Vault in Kubernetes
Enhanced Security and Encryption
Dynamic and Expiring Credentials
领英推荐
Centralised Secrets Management
Secure Integration with Kubernetes
Compliance and Audit Readiness
Use Cases of HashiCorp Vault in Kubernetes
1. Secure Database Credentials
Instead of storing static database passwords in Kubernetes Secrets, Vault dynamically generates short-lived database credentials per application request.
Benefit: Eliminates the risk of leaked or misused credentials.
2. Cloud API Key Management
Applications running in Kubernetes often require API keys for AWS, GCP, or Azure. Vault can issue short-lived API keys dynamically, removing the need for static keys.
Benefit: Enhances security by rotating API keys and limiting their usage.
3. TLS Certificate Management
Vault can act as a certificate authority (CA), issuing TLS certificates for microservices within Kubernetes.
Benefit: Ensures encrypted communication between services, eliminating the risks of manually managed certificates.
4. Multi-Tenant Secret Isolation
In a multi-tenant Kubernetes cluster, Vault namespaces allow teams to isolate secrets per project, team, or environment.
Benefit: Provides complete segregation of secrets, preventing cross-access.
5. Automated Secret Rotation for DevOps Pipelines
CI/CD pipelines often require secrets to deploy applications. Vault integrates with Jenkins, GitHub Actions, and GitLab CI/CD to fetch secrets securely at build time.
Benefit: Prevents hardcoded credentials in repositories and pipeline logs.
Future of HashiCorp Vault in Kubernetes
HashiCorp Vault is an indispensable tool for securing secrets in Kubernetes, providing robust encryption, access control, and automated secret rotation. By integrating Vault with Kubernetes, organisations can enhance security, reduce operational overhead, and improve compliance.
Key Takeaways: