Guarding the Gateways: Navigating the Wild West of BGP Security
Introduction
The Border Gateway Protocol (BGP) is the backbone of internet routing, enabling the transfer of data across the world by determining the best paths between different networks. As the de facto standard for routing between Autonomous Systems (AS), BGP plays a crucial role in maintaining global connectivity. However, the protocol’s design, originating from a more trust-oriented era of networking, is not without its flaws. These weaknesses, particularly in the realm of security, have led to numerous incidents that highlight the need for improved safeguards in BGP deployments.
This essay explores the security challenges inherent in BGP, examines existing and emerging solutions, and discusses the future direction of BGP security.
Fundamentals of BGP
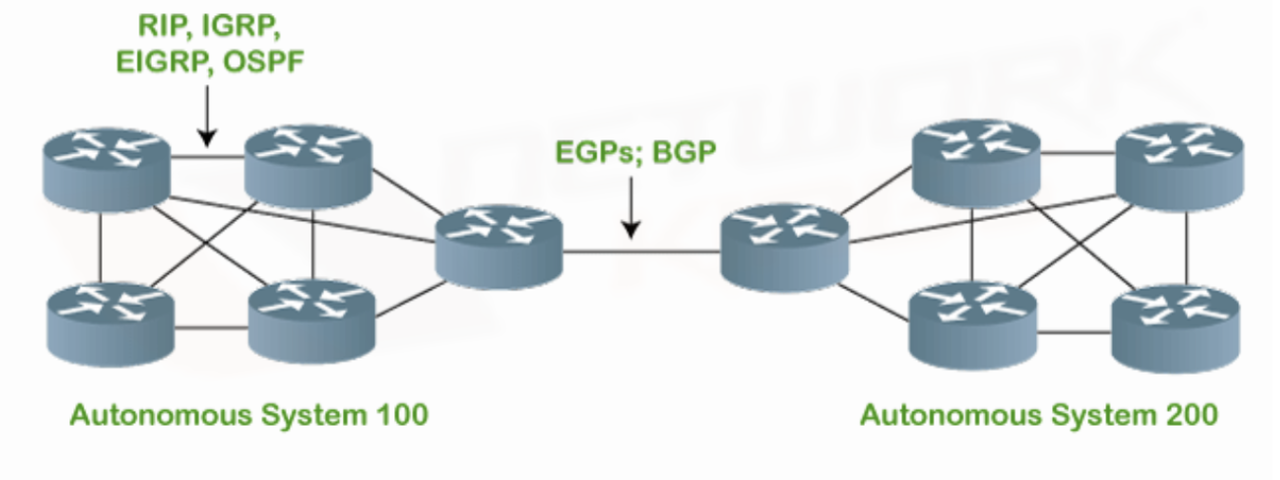
BGP is a path vector protocol that facilitates routing decisions across the Internet by using the concept of Autonomous Systems (ASes). Each AS represents a network or a collection of networks managed by a single organization. BGP sessions, which can be either Internal (IBGP) or External (EBGP), are established between routers to exchange routing information.
IBGP vs. EBGP
IBGP sessions occur between routers within the same AS, while EBGP sessions are established between routers in different ASes. IBGP relies on a full-mesh topology or the use of route reflectors to distribute routes efficiently within the AS. EBGP, on the other hand, handles the propagation of routing information between ASes and is the key component that enables global internet routing.
Route Selection Process
BGP routers choose the best path based on various attributes, such as the AS path length, origin, and multi-exit discriminator (MED). The selected routes are then advertised to other BGP peers. This process is essential for ensuring data is routed efficiently across the globe.
Common Configurations
BGP configurations vary widely depending on the needs of the network. Some common practices include prefix filtering, route aggregation, and the use of BGP communities to tag routes for specific handling by other networks.
Despite its critical role, BGP’s design does not inherently include robust security measures, making it susceptible to various types of attacks.
Security Challenges in BGP
?BGP’s security challenges stem from its original design assumptions, which relied on trust between network operators. However, in today’s internet landscape, where bad actors can exploit vulnerabilities for malicious purposes, this trust can be easily undermined.
Route Hijacking
One of the most significant security issues in BGP is route hijacking. This occurs when a malicious AS advertises IP prefixes that it does not own, causing traffic destined for those IP addresses to be misrouted through the attacker’s network. Route hijacking can lead to data interception, service disruption, and even complete denial of service for the affected IP ranges.
Route Leaks
A route leak happens when an AS mistakenly or maliciously advertises prefixes learned from one of its peers or customers to another peer or upstream provider. This can cause suboptimal routing and congestion on the global internet, leading to degraded performance or outages.
Lack of Authentication
Traditional BGP implementations lack mechanisms for authenticating the legitimacy of route announcements. This opens the door for attackers to inject false routes into the BGP tables of other routers, potentially disrupting large portions of the internet.
?These challenges underscore the need for network operators to adopt more stringent security practices and for the development of enhanced security protocols for BGP.
?BGP Security Mechanisms
?To mitigate the risks associated with BGP, several security mechanisms have been developed. These mechanisms range from basic filtering techniques to more advanced cryptographic methods.
Prefix Filtering
Network operators can implement prefix filtering to control which IP prefixes are advertised to or accepted from BGP peers. By only allowing legitimate prefixes, operators can reduce the risk of accepting bogus routes.
Route Filtering
Similar to prefix filtering, route filtering enables operators to block specific routes based on various criteria, such as AS path or origin. This helps in preventing route leaks and hijacks.
BGP Communities for Security
BGP communities are tags applied to routes that can influence how they are treated by other routers. Operators can use communities to enforce routing policies that enhance security, such as preventing routes from being advertised to certain peers.
RPKI (Resource Public Key Infrastructure)
RPKI is a cryptographic system that allows IP address holders to certify which ASes are authorized to announce their prefixes. By validating routes against these certificates, BGP routers can reject invalid route announcements, reducing the likelihood of hijacks.
BGPSEC
BGPSEC is an extension to BGP designed to provide cryptographic validation of AS paths. Each AS in the path digitally signs its route advertisement, allowing downstream routers to verify the authenticity and integrity of the AS path. While BGPSEC offers stronger security guarantees, its adoption has been slow due to the increased computational overhead and the need for widespread deployment.
Case Studies of BGP Security Incidents
Real-world incidents provide valuable insights into the vulnerabilities of BGP and the effectiveness of various security measures.
Notable BGP Hijacks
In April 2010, China Telecom briefly hijacked approximately 15% of the global internet traffic by incorrectly advertising more than 37,000 prefixes. This incident highlighted the ease with which a misconfigured or malicious AS could disrupt global communications.
Route Leaks Analysis
In June 2019, a route leak by a European network operator caused widespread disruption across multiple services, including Google Cloud. The leak resulted from a misconfiguration that propagated incorrect routes to upstream providers, causing traffic to be blackholed or rerouted through unintended paths.
Lessons Learned
These incidents underscore the importance of implementing security measures such as prefix filtering, route validation, and close monitoring of BGP sessions. They also highlight the need for global cooperation among network operators to address BGP security challenges.
Future of BGP Security
The future of BGP security lies in the continued development and adoption of new technologies and standards, as well as greater collaboration among the global networking community.
Emerging Technologies
Advances in RPKI and BGPSEC are critical to improving BGP security. However, for these technologies to be effective, they must be widely adopted by network operators worldwide.
Collaboration
Network operators must work together to share information about BGP incidents and best practices for securing BGP sessions. Initiatives such as the Mutually Agreed Norms for Routing Security (MANRS) encourage operators to commit to improving the security and resilience of the global routing system.
Protocol Enhancements:
The BGP protocol itself may require further enhancements to address security concerns. This could include more stringent requirements for route validation, the incorporation of stronger cryptographic techniques, and the development of new mechanisms for detecting and mitigating attacks.?
Conclusion
Securing BGP is critical to maintaining the stability and reliability of the global internet. While significant progress has been made in developing tools and techniques to protect BGP, challenges remain. Network operators must remain vigilant and proactive in adopting these measures, and the networking community must continue to innovate and collaborate to address emerging threats. The ongoing evolution of BGP security will be essential in ensuring the internet remains a secure and resilient platform for global communication.
Global Chief Marketing, Digital & AI Officer, Exec BOD Member, Investor, Futurist | Growth, AI Identity Security | Top 100 CMO Forbes, Top 50 CXO, Top 10 CMO | Consulting Producer Netflix | Speaker | #CMO #AI #CMAIO
7 个月Scott, thanks for sharing! How are you doing?