Dynamic Application Security Testing - Fortify WebInspect
Steve Roberts
I help the U.S. DOD and INTEL Community acquire enterprise software applications that Develop, Test, and Secure AGILE enterprise software applications. #ALM_Octane #LoadRunner #UFT #Fortify #WebInspect #DevSecOps
The Threat is Real!
As cyber-attacks and data breaches continue to rise, it’s more important than ever to ensure that web applications are secure. Fortify is the leader in static application security testing (SAST) and is widely used through out the U.S. Public and Private sectors. SAST scanning, however, is not enough to mitigate all threats, vulnerabilities and exposures, particularly in deployed web applications. Dynamic application security testing (DAST) tools need to be made part of a comprehensive defense in depth arsenal. There are a number of DAST tools choose from, but there’s only one that holds the trusted Fortify name … WebInspect.
WebInspect - A Brief History
WebInspect dates back to the early 2000s when it was initially developed by a company called SPI Dynamics (also known as Security Performance Intelligence Dynamics). Founded by Caleb Sima and based in Atlanta, Georgia, SPI Dynamics aimed to address the emerging challenges of web application security to help organizations protect their web-based assets from potential threats - it quickly became a leading provider for web application security testing. SPI Dynamics developed several notable products and technologies, notably its flagship product, WebInspect that gained widespread recognition and became a key tool for identifying and addressing security flaws in web applications. WebInspect utilized dynamic scanning techniques to interact with web applications, identify vulnerabilities, and provide detailed reports to help developers and security professionals mitigate various web application risks.
In 2007, Hewlett-Packard (HP) recognized the potential of WebInspect and acquired SPI Dynamics. Over the years, HP continued to enhance and improve WebInspect's capabilities, and the tool evolved to support the latest web technologies and security standards, enabling users to effectively detect and remediate vulnerabilities in web applications. WebInspect's features include dynamic scanning, which involves interacting with web applications to identify potential vulnerabilities and comprehensive reporting which provided detailed analysis of security flaws and recommended remediation actions.
In 2017, HP split into two separate companies: Hewlett Packard Enterprise (HPE) and HP Inc. with HPE retaining the enterprise-focused businesses including the security division. In 2019, Micro Focus acquired the software assets of HPE, including the WebInspect; and in 2023, OpenText purchased Micro Focus.
Protecting our National Security Interests
There are numerous DoD specifications and Guides that require DAST security controls such as: Navy RAISE 2.0, DoD Enterprise DevSecOps Reference Design, DoD Enterprise DevSecOps Fundamentals, etc. And there are numerous DoD specifications and Guides that call for DAST security controls including: Navy RAISE 2.0, DoD Enterprise DevSecOps Reference Design, DoD Enterprise DevSecOps Fundamentals, etc.
WebInspect has had the benefit of being used the U.S. DoD and Intel Community for many years - it is "tried and true". In addition to five outstanding features that I will shortly describe, WebInspect is certified to be used for: NIST 800-53 SA-11, DISA STIG compliance, FITARA cybersecurity scores, Executive Measure 3.2, Continuous Authority to Operate (cATO); plus it is part of the DoD's Information Assurance Approved Products List (IA APL).
Why WebInspect?
Allow me to highlight the top five features of WebInspect that make it stand out above the rest: 1) WebInspect’s comprehensive scanning capabilities, 2) Automatic crawling and scanning, 3) Accurate and actionable results, 4) Integration with other tools, and 5) Scalability and flexibility -- these features make WebInspect an excellent choice for any organization looking to secure their web applications. I want to drill down on each of these features:
Comprehensive Scanning Capabilities
The U.S. Department of Defense and Intelligence Community require web application security tools that can handle large, complex applications and accurately identify vulnerabilities, making WebInspect is a great choice.
WebInspect's comprehensive scanning capabilities have proven to be effective in identifying a wide range of vulnerabilities including SQL injection, cross-site scripting (XSS), buffer overflow, and many others. WebInspect also supports a variety of programming languages and web application frameworks, making it a versatile tool for all types of web applications.
In addition, WebInspect has the ability to scan web applications that are not publicly accessible. Since many U.S. agencies' web applications are behind firewalls or require a specific connection, it is challenging for traditional web application scanners to assess them. WebInspect has the ability to scan web applications regardless of their accessibility, making it a valuable tool for these secure organizations.
领英推荐
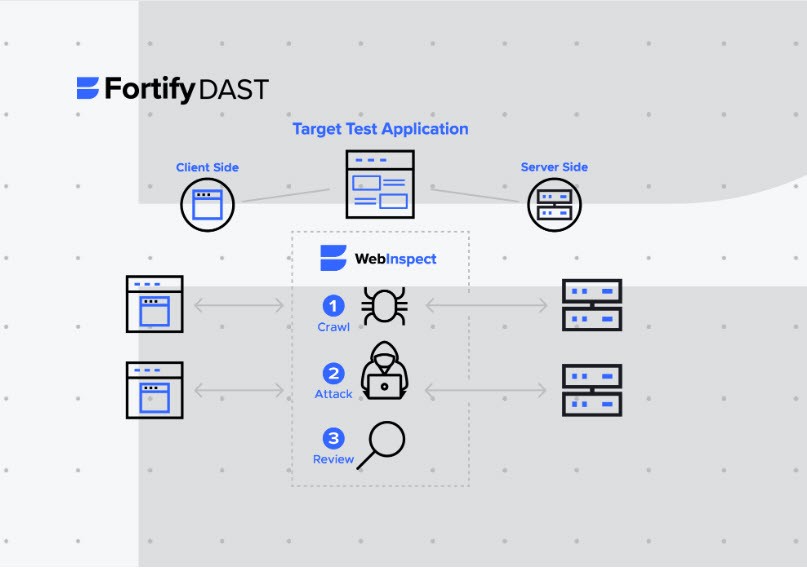
Automatic Crawling and Scanning
WebInspect can scan large, complex web applications efficiently, reducing the amount of manual effort required to identify vulnerabilities. Further, WebInspect doesn’t require hours to manually configuring the tool or selecting which pages to scan. WebInspect automatically crawls your web application, identifies all pages, and scans them for vulnerabilities - this saves time and ensures that no pages are missed during the scanning process. The tool requires minimal user intervention, making it easy to use. WebInspect can even help organizations stay ahead of emerging threats by automatically detecting new pages or functionality.
With WebInspect, you can inspect parts of the application that may not be discoverable through normal crawling, collect information about the internal behaviors of an application during dynamic tests, and detect new types of vulnerabilities – all in real-time. As a result, you filter out false positives, confirm vulnerabilities, and provide development teams with more actionable details, such as stack trace and line of code detail.
Accurate and Actionable Results
Unlike some web application security tools that generate false positives or vague results, WebInspect is known for its accurate and actionable results - caveat here, no tools are perfect; however, WebInspect provides detailed information about vulnerabilities, including the severity of each issue and how to fix it which helps you prioritize and address vulnerabilities quickly and effectively.
The goal is to provide actionable results as turnkey of a manner as possible. When used together, WebInspect and Fortify SCA can stimulate the application through automated, external security attacks and then gather internal, code-level vulnerability information by observing the attacks in the code as they happen. You can then uncover real issues more quickly, determine root causes, and deliver more actionable results to development for remediation.
WebInspect reporting provides a wealth of information, including the severity of each vulnerability, the location of said vulnerability, and the steps that are required to remediate it. This level of detail allows organizations like yours to prioritize your remediation efforts and ensure that you are addressing the most critical vulnerabilities first.
Integration with Other Tools
Another great feature of WebInspect is its integration with various systems and technologies to enhance its functionality and compatibility with existing security processes. One of the systems WebInspect can integrate with is Fortify static code analysis (SCA) which makes it easier to manage all aspects of your security program from a single platform. WebInspect also integrate with ALM Octane which allows seamless collaboration between security and development teams, making it easier to prioritize and address vulnerabilities throughout the software development lifecycle. This enables continuous DevSecOps into your agile SDLC process.?
WebInspect integrates with development and testing tools such as integrated development environments (IDEs) and continuous integration/continuous deployment (CI/CD) pipelines. This allows for seamless integration of security testing into the software development lifecycle. These are just a few examples where WebInspect can integrate to improve DevSecOps, maximizing your investment and providing maximum security.
Scalability and Flexibility
WebInspect has proven to be up to the task whether you have a small web application or a large complex one. WebInspect's scalability and flexibility have made it the popular choice for organizations and agencies of all sizes, including some of the most security-conscious agencies out there. When it comes to scalability, WebInspect has been proven to accommodate the needs of organizations, scanning multiple applications simultaneously, allowing for efficient and comprehensive security assessments. Additionally, WebInspect provides flexibility in terms of deployment options. It can be deployed on-premises, in the cloud, or as a managed service. This flexibility allows you to choose the deployment method that best suits your organization's requirements, infrastructure, and security policies.
In Conclusion
If you're part of a security-conscious department or organization, you can rest assured that WebInspect has been utilized by the most challenging security environments in the world. Its comprehensive scanning capabilities, automatic crawling, scanning, accurate and actionable results, integration with other tools, and scalability and flexibility make it a standout. ?
Great read, Steve, thanks for sharing such a detailed analysis!
Building Brands | Driving Digital Growth | Committed to Application Precision with QA Testing | Sr. Digital Marketer At Testrig Technologies
1 年Thank you for the clear explanation! Testing application has become crucial in today's world, and it has become the top priority for companies to implement security testing process.