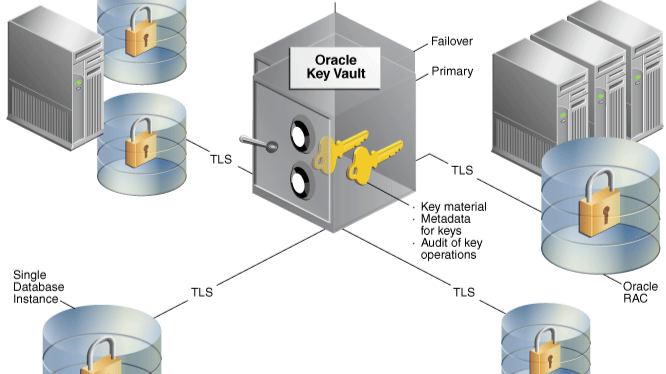
Configuring Transparent Data Encryption (TDE) with Oracle Key Vault (OKV) as the keystore in Oracle 19c Database
This guide focuses on configuring Transparent Data Encryption (TDE) with Oracle Key Vault (OKV) as the keystore in Oracle 19c, eliminating local file wallets.
Prerequisites
Step 1: Configure the Database for OKV Integration
1.1 Set WALLET_ROOT and TDE_CONFIGURATION
ALTER SYSTEM SET WALLET_ROOT='/u01/app/oracle/wallets' SCOPE=SPFILE;
ALTER SYSTEM SET TDE_CONFIGURATION='KEYSTORE_CONFIGURATION=OKV' SCOPE=BOTH;
SHUTDOWN IMMEDIATE;
STARTUP;
Note: In Oracle 19c, TDE_CONFIGURATION replaces deprecated sqlnet.ora settings for wallet location.
Step 2: Enroll the Database in Oracle Key Vault
2.1 Install and Configure the OKV Client (okvutil)
unzip okvrestcli-<version>.zip -d /opt/oracle/okv
export OKV_HOME=/opt/oracle/okv
mkdir -p $OKV_HOME/conf
OKV_REST_SERVER=https://<OKV_IP>:5696
OKV_WALLET_ROOT=$WALLET_ROOT/okv # Align with WALLET_ROOT
2.2 Enroll the Database as an OKV Endpoint
okvutil endpoint create --generate-token --unique-alias <DB_UNIQUE_NAME>
okvutil deploy --token <generated_token>
Step 3: Create the TDE Master Encryption Key in OKV
3.1 Generate the Master Key
Open the Keystore (if not already open):
ADMINISTER KEY MANAGEMENT SET KEYSTORE OPEN IDENTIFIED BY '<OKV_WALLET_PASSWORD>';
Generate the Master Key:
ADMINISTER KEY MANAGEMENT CREATE KEY USING TAG 'TDE_MASTER_KEY_19C' IDENTIFIED BY '<OKV_WALLET_PASSWORD>' [CONTAINER=ALL];
3.2 Verify Key Creation
Check for the key in OKV via the console (navigate to Security Objects > Keys) and in the database:
SELECT KEY_ID, TAG, CREATION_TIME FROM V$ENCRYPTION_KEYS;
Step 4: Encrypt Data Using TDE
4.1 Encrypt Tablespaces
CREATE TABLESPACE encrypted_ts
DATAFILE '+DATA' SIZE 1000M
ENCRYPTION USING 'AES256'
DEFAULT STORAGE(ENCRYPT);
ALTER TABLESPACE USERS ENCRYPTION ONLINE USING 'AES256' ENCRYPT;
4.2 Validate Encryption
SELECT TABLESPACE_NAME, ENCRYPTED FROM DBA_TABLESPACES;
SELECT WRL_TYPE, STATUS FROM V$ENCRYPTION_WALLET;
-- Expected output: WRL_TYPE should indicate "OKV" and STATUS should be "OPEN"
Troubleshooting
Database cannot connect to OKV:
Key creation fails:
Wallet not open:
Open the keystore manually if necessary:
ADMINISTER KEY MANAGEMENT SET KEYSTORE OPEN IDENTIFIED BY '<OKV_WALLET_PASSWORD>';
Oracle 19c-Specific Notes
References
By following these steps, your Oracle 19c database will use OKV for centralized TDE key management, enhancing security and compliance.
#Oracle #DB #Vault #OKV #TDE #OracleKeyVault #KeyVault