In this article, i’ll explore how to architect and deploy a modern serverless API solution using various AWS services, including Application Load Balancer (ALB), API Gateway, Cognito, Lambda, and DynamoDB.
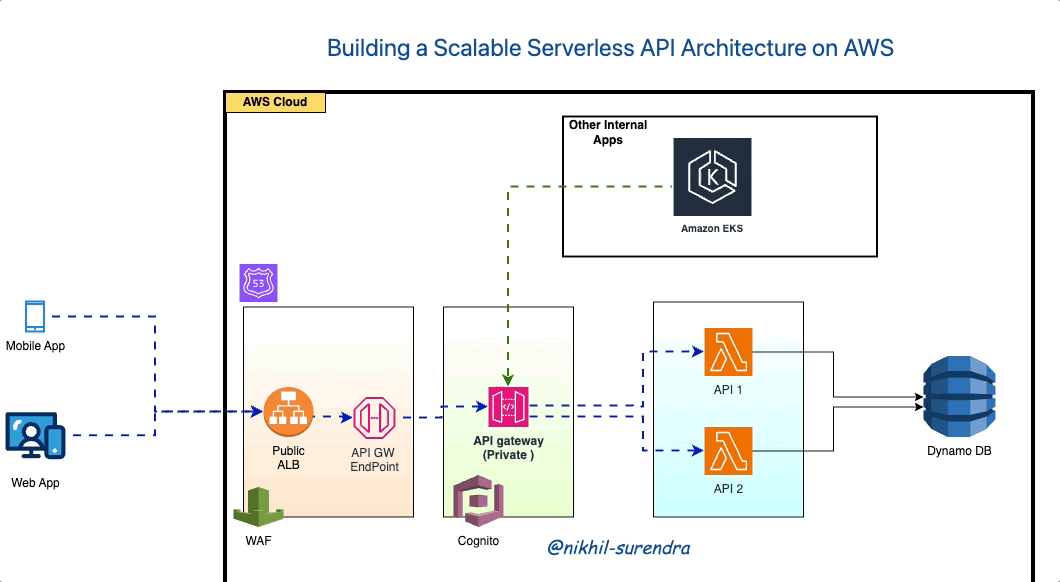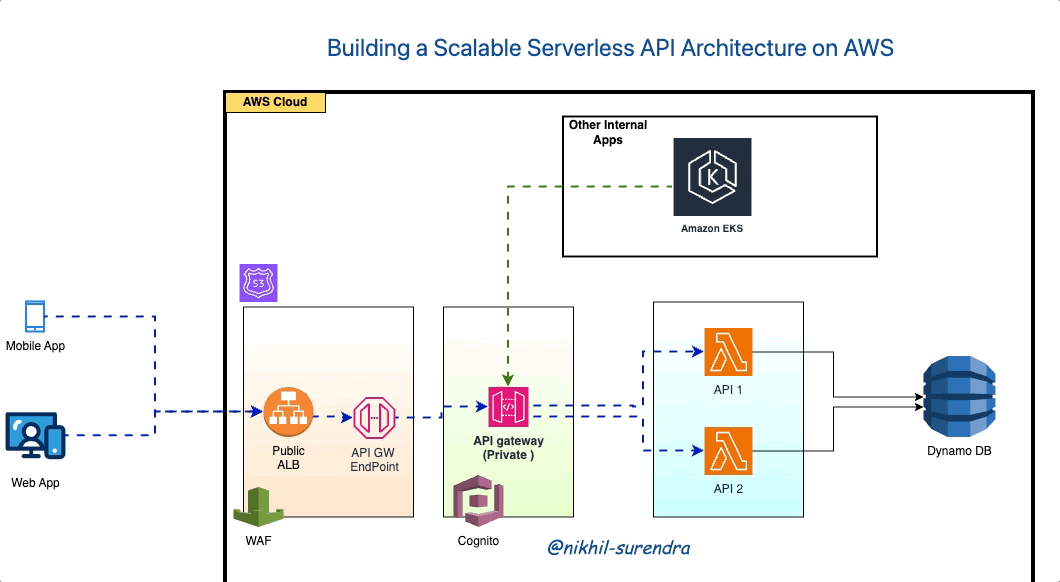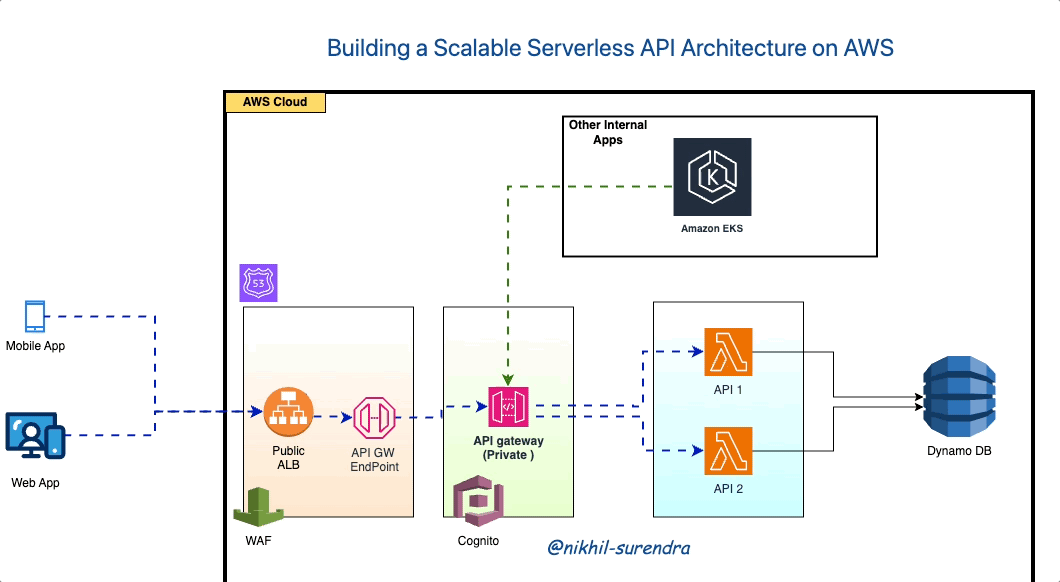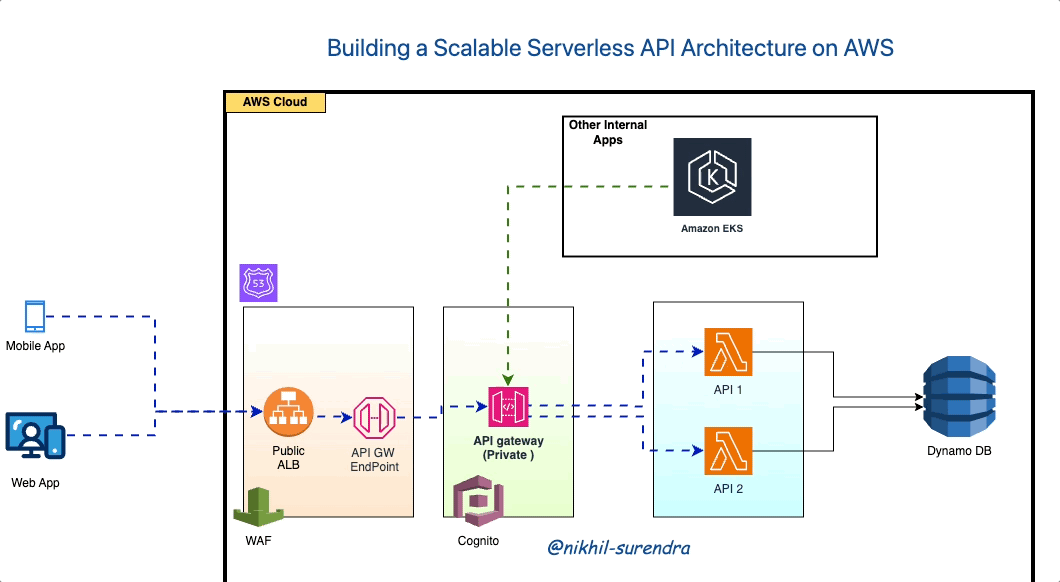
Architecture Overview
Components:
- ALB: Receives incoming HTTP/HTTPS requests and forwards them private API gateway via vpc endpoint.
- API Gateway: Acts as the entry point for API requests, provides request/response transformation, and integrates with Lambda functions and other AWS services.
- Cognito Authorizer: Authenticates and authorizes API requests using Cognito user pools or identity pools, ensuring secure access to resources.
- WAF — is a web application firewall that helps protect web applications and APIs from attacks. It enables you to configure a set of rules called a web access control list (web ACL) that allow, block, or count web requests based on customizable web security rules and conditions that you define.
- Resource Policy: Defines access control policies for API Gateway resources, restricting access based on user identity , client IP addresses.
- VPC Endpoint- To access your private API once it’s deployed, you need to create an interface VPC endpoint for it in your VPC. The VPC endpoint for API Gateway will must be multi AZ, providing an Elastic Network Interface (ENI) in each private subnet.
- Lambda Functions: Business logic and data processing logic implemented as serverless functions triggered by API Gateway requests.
- DynamoDB: NoSQL database for storing and retrieving application data, providing low-latency access to structured data with automatic scaling.
- Route53 — Amazon Route 53 is a highly scalable and reliable Domain Name System (DNS) web service provided by Amazon Web Services and will used to create DNS for Loadbalancer.
Implementation Steps
- Create ALB: Create an Public Application Load Balancer in your vpc and configure routing rules to forward incoming HTTP/HTTPS traffic to target groups. The ALB is configured with an HTTPS listener, linked to a target group containing the IP addresses of the ENIs.
- Create API Gateway: Define RESTful APIs using API Gateway, configure endpoints, request/response transformations, and integrate with backend Lambda functions. Private api gateway can be access by the url <<api_id>>-<<vpc_endpoint_id>>.execute-api.<<region>>2.amazonaws.com/<<stage>>
- Configure Cognito: Create a user pool and/or identity pool in Cognito, configure authentication flows, and set up user sign-up, sign-in, and access control policies.
- Define Resource Policies: Configure resource policies in API Gateway to control access to API resources based on identity that restrict the execute-api.
- Deploy Lambda Functions: Deploy the Lambda function in your VPC on private subnet and assigned a role that can be assumed by the lambda to execute , create log and connects to the dynamo DB table.
- Set up DynamoDB: Create DynamoDB tables to store application data, define table schemas, and configure read/write capacity units and auto-scaling settings.
- Integrate Components: Connect API Gateway endpoints with ALB and API Gatway functions, configure authorization mechanisms using Cognito authorizers, and ensure seamless communication between components.
- Any application running internal can connect to the api gateway using https://api-id-vpc-endpoint-id.execute-api.region.amazonaws.com/stage.
Sample resource policy for API Gateway to execute via VPC Endpoint
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "execute-api:Invoke",
"Resource": "arn:aws:execute-api:<<AWS_REGION>>:<<YOUR_AWS_ACCOUNT_ID>>:<<API_ID>>/*",
"Condition": {
"StringNotEquals": {
"aws:aws:SourceVpce": "<<YOUR_VPC_ENDPOINT>>"
}
}
}
]
}
Best Practices and Considerations
- Implement proper authentication and authorisation mechanisms using Cognito and API Gateway authorisers to protect your APIs from unauthorised access.
- WAF can be deployed in front of API endpoints to protect against API abuse, unauthorised access, and data exfiltration attempts by malicious actors.
- Design your architecture for horizontal scalability by leveraging auto-scaling capabilities of ALB, Lambda, and DynamoDB to handle varying levels of traffic.
- Configure proper reserved concurrency to manage concurrent requests and provisioned concurrency to pre-initialized execution environments (Pre-warm) to avoid latency on api response.
- Configure throttling and burst level for scaling of API gateway based on loads.
The solution is based AWS services that has high-availability by default across Availability Zones in the AWS Region. Requests throttling can be configured on each private API Gateway to protect the underlying resources from being overwhelmed.
- Use AWS CloudWatch to monitor API Gateway usage metrics, Lambda function invocations, ALB access logs, and DynamoDB performance metrics for real-time monitoring and troubleshooting.
- Optimize costs by using serverless architectures
- Leveraging AWS Free Tier offerings
- Scaling resources based on actual usage patterns to minimize operational expenses.
Conclusion
If you’re building a web application, mobile app backend, or micro services architecture, AWS provides the tools and services you need to succeed in the cloud. By leveraging the power of serverless AWS services like ALB, API Gateway, Cognito, Lambda, and DynamoDB, you can build a highly scalable, secure, and cost-effective API architecture to support your application’s requirements..
Chief of Strategic Accounts - Americas at Xebia
11 个月Great Article Nikhil Surendran ! Xebia #Authority Matthew S. Gosselin Rajat Kanwar Gupta Shekhar G.